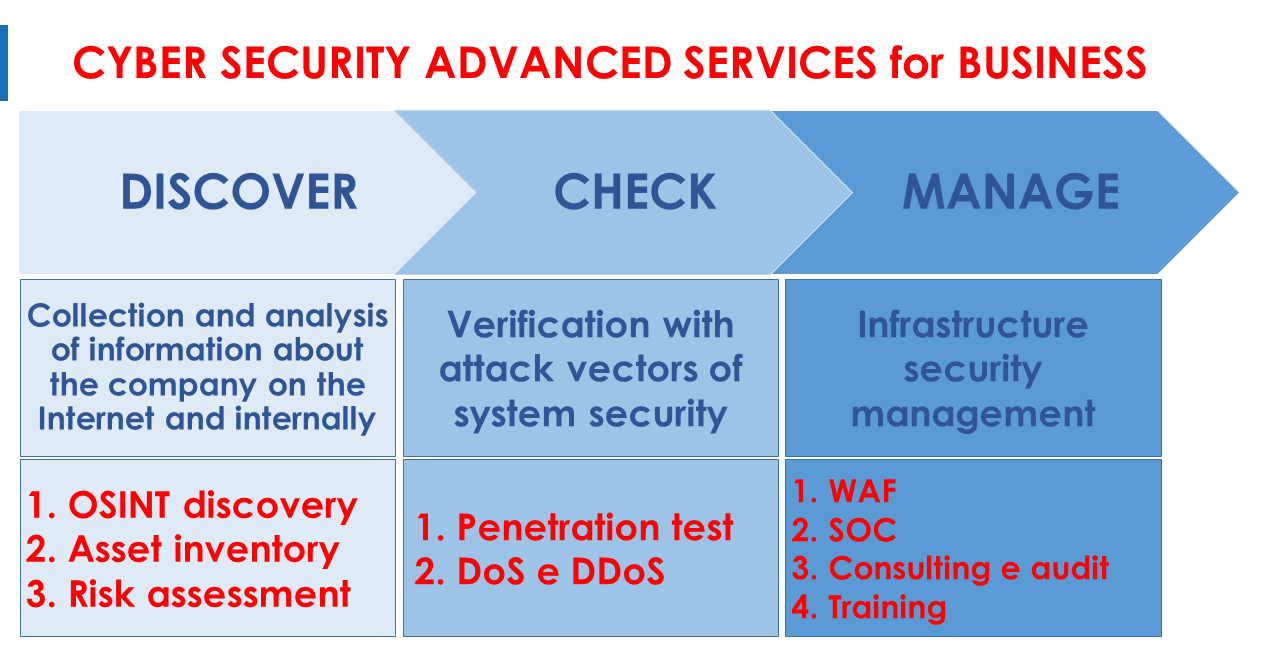
DISCOVER
LET'S FIND OUT ALL THE INFORMATION ON THE INTERNET
Any cyber attack begins with the collection of public information about the domain, so it is critically important to know it, as hackers can do, in order to adequately protect yourself.
Information gathering is done by a proprietary tool that uses OSINT (Open Source INTelligence) methodology to analyze all public sources and collect existing information. This immense amount of data is then analyzed by our certified cyber specialists who select meaningful information and eliminate false positives.
The results from this service are:
WE DETECT AND ANALYZE ALL ICT ASSETS IN THE COMPANY
The IT asset inventory service is used to detect, classify and learn about the characteristics of all technological elements in the company, such as personal computers, servers, mobile devices, printers, IoT, etc.
Once placed in a special repository, all hardware and software characteristics are collected by identifying the installed versions, and thanks to the connection with device and sw databases, update levels are verified by reporting vulnerabilities and the relative level of risk present in the sw versions used and any patches to be applied.
The results from this service are:
WE IDENTIFY AND ASSESS ICT RISKS TO THE BUSINESS
Our IT risk management service is used to identify, assess and manage the risks associated with the use of technology within the company and their impacts on the business.
The risks are analyzed from various aspects particularly data security, the readiness of the systems for use by the business in carrying out its activities, and compliance with various applicable regulatory requirements (e.g., personal data protection).
The results from this service are:
CHECK
Penetration Test
DoS o DDoS attacks:
DoS means Denial of Service and DDoS means Distributed DoS. The purpose is to understand the level of sensitivity of various assets to an overload of requests that can engender system failure and to assess the effects this disruption can have on the business
The results of these services are:
MANAGE
Through the remote deployment of our WAF in the cloud it is possible to trace a domain-level security perimeter and through the ruleset engine using machine learning algorithms to have instant, continuous and constant protection.
Remote specialist support, integrated with the WAF service, managed with our experts available 24x7 enables even medium-sized companies to have, at an affordable cost, coverage in terms of managing their company's security comparable to that of large organizations.
Our ICT security and architecture specialists can support you in designing your infrastructure with a view to maximizing security and service continuity to ensure the highest level of peace of mind.
Auditing activities on relevant standards (ISO 27001, personal data protection, mandatory standards,...) supports your company in achieving certification or regulatory compliance goals.
We can demonstrate live with a custom demo what we can do for your specific needs. Please feel free to contact us!
© Advanced CGS Group SA 2015-2024 - Powered by SpoonDesign